Phishing Campaigns for Emotet Malware
 69836
69836
21 September, 2020
Publication Link
Phishing Campaigns for Emotet Malware
Researchers first discovered a Trojan horse known as (Emotet) in 2014, which was then targeting banks. Emotet was originally designed as a banking malware that attempted to sneak onto your computer and steal private and sensitive information. Advanced versions of this malware have the ability to send spamming mails and emails contacting malware without the need of user intervention. Emotet uses features that can help it avoid detection by antivirus and antimalware softwares.
Emotet is spread by spam / junk emails (malspam). The user may be infected via either malicious script, macro-enabled document files, or a malicious link. Emails may contain familiar brand names to appear as a legitimate email. Emotet may try to persuade you to click on malicious files or links using tempting language such as "Your order invoice" or "Payment details" or perhaps a shipment coming from a well-known delivery company and others.
The initial infection is when the user clicks on a malicious file or link, after that your device will be infected and it will be a part of a huge compromised network of computers known as a botnet(1) and will act as a compromised computer (bot) to try to spread Emotet to all your contact lists without the need of your interference.
The Bot Master controls the network of the compromised computers through a command and control channel (C&C) to manage its network, implement its attacks, and spread Emotet to the largest number of users.
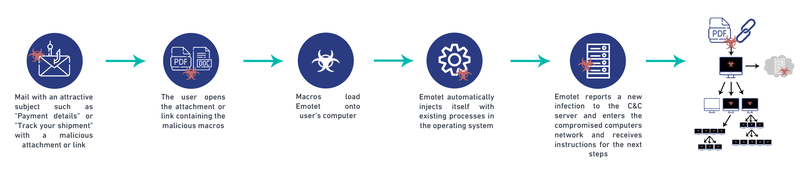
Picture 1: infection method by Emotet via emails
Saudi CERT recommends the following best practice and recommendations to organizations:
- Use Group Policy Object to set a Windows Firewall rule to restrict inbound SMB communication between client systems.
- Activate the Sender Policy Framework (SPF), which enables the organizations to register the addresses of servers that are authorized to send e-mail. It also checks the IP addresses of incoming e-mail messages by comparing them with the SPF content in the source’s DNS.
- Use antivirus and antimalware programs, with automatic updates of signatures and software, on clients and servers.
- Apply security patches and updates immediately after their release and after appropriate testing.
- Implement filters at the email gateway to filter out emails with known malspam indicators, such as known malicious subject lines, and block suspicious IP addresses.
- Consider blocking file attachments that are commonly associated with malware, such as .dll and .exe, and attachments that cannot be scanned by antivirus, such as .zip files.
- Adhere to the principle of least privilege, ensuring that users have the minimum level of access required to accomplish their tasks.
- Implement Domain-Based Message Authentication, Reporting & Conformance (DMARC), a validation system that minimizes spam emails by detecting email spoofing using Domain Name System (DNS) records and digital signatures.
- If your organization does not have a policy regarding suspicious emails, consider creating one and specifying that all suspicious emails should be reported to the Cybersecurity or IT department.
- Mark emails sent from an external source with a flag or a banner indicating that they are from an external source. It will help the employee in detecting suspicious emails.
- Provide employee training on social engineering and phishing, and urge employees not to open suspicious emails, click on links in emails, or post sensitive and/or private information online, and never provide usernames, passwords, or personal information upon reply on any request.
- Educate employees by hovering over the link with the mouse to verify the link before clicking on it.
If the organization or the user believes that they have been infected with Emotet, Saudi CERT advises the following actions:
- Identify infected devices, shutdown and isolate them from the network.
- Identify the source of the infection.
- Disconnect the network from the Internet temporarily to perform identification, prevent reinfections, and stop the spread of the malware.
- Do not log into infected systems using an "administrator" accounts.
- Reformat the infected device.
- After reviewing the systems to confirm the presence or absence of Emotet indicators, move the uninfected systems to a virtual containment local area network away from the affected network.
- Reset the password for all users.
- Reset the password for applications that may have had stored credentials on the compromised machine.
- Review the log files and the Outlook mailbox rules associated with the infected user account to ensure further compromises have not occurred.
General Emotet malware prevention tips for individuals:
- Because Emotet often hides in Microsoft Office files and needs macros to install malware, disable macros, or just allow digitally signed macros.
- Update the operating system, antivirus and browser from their official source and enable automatic updating.
- Back up your system and files periodically.
- Use antivirus and firewall and update them periodically.
- Avoid opening suspicious or anonymous links and attachments.
- Do not download attachments before scanning them and confirming the sender.
- Enable unsolicited bulk emails filtering (Spam).
- Hover over the link before clicking on it to make sure the link is legitimate.
(1) Botnet: A collection of compromised computers (bots) running malicious applications without the knowledge of the user via a command and control infrastructure.

 The official site for Saudi CERT
The official site for Saudi CERT





